图1 系统架构图

支持隐私保护的物联网数据筛选方案
暂无标题
- 西安电子科技大学学报 2023年50卷第4期 页码:45-53
DOI:10.19665/j.issn1001-2400.2023.04.005
扫 描 看 全 文
引用本文
阅读全文PDF
摘要
随着工业5.0的推广,物联网需要对运行数据进行实时采集和上传存储。为了更精确地描述和分析物联网工作状态,需要采集高精度实时数据。然而物联网不同类型数据的混合存储会降低数据分析效率,为了提高混合存储环境中的数据分析效率,需在数据上传过程中对数据进行分流来实现数据的分类存储。传统的数据分流方法只能对明文数据依据其来源来实现分流,而明文数据的来源信息会泄露设备的身份隐私。因此,如何在不泄露隐私的基础上,通过密文分流实现物联网数据的分类存储,成了物联网数据安全管理亟待解决的问题。文中提出一个隐私保护的物联网数据筛选方案,在保障内容和设备身份隐私的基础上,通过数据发送设备的身份生成筛选陷门来设定中继节点设备数据筛选规则,在数据上传阶段对数据进行筛选分流,将混合的异源数据按数据来源分类为同源数据进行分别存储,为后期的数据访问控制及分析提供服务支撑。实验结果表明,所提方案比同类型的方案执行效率更高。
Abstract
With the development of industry 5.0,the operational data need to be collected and uploaded in real time in the practical Internet of Things (IoT).To describe and analyze the working state of the IoT more precisely,high accurate and real-time data are required.Then,in practical applications,many different types of IoT data are stored together without classifying,which could reduce the efficiency of data analysis.In order to improve the efficiency of data analysis in the hybrid data storage environment,it is necessary to use the method of data shunting in the process of data upload to realize the classified storage of data.However,the traditional data shunting method shunts the plaintext data according to its source identity,during which the source information on the plaintext data will leak the identity and privacy of the IoT devices.Therefore,how to realize the classified storage of these IoT data through the data shunting without revealing the privacy has become an urgent problem to be solved in the security management of the IoT data.In this paper,a new privacy-preserving IoT data filtering scheme is proposed.On the basis of maintaining the context and device identity privacy,each data filtering rule is set by a filtering trapdoor,which is computed from the identity of the data source device.Then,the data can be classified and routed by the relay nodes following the given rules in the data uploading phase,from which the heterologous data can be classified and the homologous data are stored together,which can help further data access control and data analysis.Experiment results show that our scheme is efficient and practical.
1 引言
随着工业5.0的推广应用,海量的物联网数据被采集以完成物联网的应用需求。为了对这些数据进行规范化管理,研究者引入了针对物联网数据的安全管理[
这些异源数据的混合存储不仅会降低后期数据分析的效率,还会使后期的数据访问控制变得更加困难[
为实现数据筛选的目标,研究者在首次提出了基于BSD开源协议的包筛选方法[
当前,加密数据筛选主要采用对数据包进行检测的技术对通过网关的流量进行监控,进而实现数据的筛选[
以上的加密数据筛选方案,主要依托于关键字可搜索加密技术[
为解决这个问题,文献[
笔者立足于物联网数据安全管理,提出了一个支持隐私保护的加密物联网数据筛选方案,实现了物联网采集数据的筛选和分流。
(1) 不仅对传输数据进行了加密,还在数据筛选时对设备身份隐私进行了保护,使得所传输数据和其对应的数据发送设备身份信息都不会泄露,从而支持数据内容隐私保护和数据发送设备身份隐私保护。此外,还通过对加密后的数据密文进行签名来确保采集数据的完整有效。
(2) 在数据上传阶段,利用中继网络中的中继节点设备组实现数据筛选,使得数据能被分类且按其类型存储到预定位置,更加有效地支持后期的数据提取与分析。
(3) 在规则设定上,通过引入时戳机制的筛选规则陷门设置,用于增强数据筛选的实时性,以灵活应对不断变化的物联网实际应用需求。
(4) 仿真实验结果评估表明,所提方案比同类型方案的执行效率更高,更加适用于实际的物联网数据采集应用。
2 系统架构设计
2.1 相关预备知识
离散对数求解困难问题:已知(G,p,g,gx),其中p为质数,g是循环群G的一个生成元,gx是G上的一个元素,求解x是困难的。
判定性Diffie-Hellman困难问题:已知(G,p,g,gx,gy),其中p为质数,g是循环群G的一个生成元,gx、gy是G上两个不同的元素,判断Z是G上的一个随机元素还是Z=gxy是困难的。
安全的对称加密算法:能通过抵抗常规分析和攻击来保证数据机密性的对称加密算法。
2.2 系统架构
该系统的架构如
在该系统的架构中,物联网终端设备节点与数据发送端事先沟通好数据采集的对称加密密钥,再用该密钥和安全的对称加密算法将采集到的数据加密并发送给数据发送端;数据发送端得到数据之后先对数据解密,然后计算出传输用的数据加密密钥,并使用安全的对称加密算法生成可以被目标用户解读的数据密文,再用数据筛选密钥生成可以被中继节点设备组匹配分流的筛选标签,接着生成用于验证数据完整性的签名,通过无线或有线网络将生成的数据密文、筛选标签和完整性签名发送到中继节点设备,在中继节点设备进行数据完整性验证之后,最后进行筛选标签和筛选陷门的匹配,匹配成功的加密物联网数据及其对应的筛选标签和完整性签名被分流存储到对应的存储服务器。筛选标签和完整性签名可以用于用户从服务器取回数据时验证所取回加密数据的完整性。
2.3 系统方案设计
文中所提的系统方案包含以下8个部分:(1) 系统设置(Setup):算法输入安全参数μ,生成系统参数P。
(2) 密钥生成:① KeygenT:算法输入系统参数P,生成系统主密钥(msk,mpk);② KeygenA:算法输入系统参数P,用户A的身份IDA,生成用户A密钥(skA,pkA);③ KeygenB:算法输入系统参数P,设备B的身份IDB,生成设备B密钥(skB,pkB)。
(3) 密钥验证(Check):算法输入系统参数P,系统主公钥mpk、验证者自己的密钥(sk,pk),进行密钥验证。若sk是有效密钥,则算法输出“1”;否则,sk不是有效密钥,输出“0”。
(4) 筛选陷门生成(Trapdoor):算法输入系统参数P,用户A的私钥skA设备B的公钥pkB和时戳t,生成t时刻的筛选规则陷门Tr。
(5) 数据密文和筛选标签生成(Index):算法输入系统参数P,设备B的私钥skB和用户A的公钥pkA,时戳t和物联网数据data,生成加密物联网数据m和用于匹配筛选的标签I。
(6) 完整性签名生成(Sign):算法输入系统参数P,设备B的私钥skB与加密物联网数据m和筛选标签I,生成用于保证数据完整性的签名σ。
(7) 完整性签名验证(Verify):算法输入系统参数P,设备B的公钥pkB与加密物联网数据m和保证数据完整性的签名σ。若σ是有效签名,则算法输出“1”;否则,σ不是有效签名,输出“0”。
(8) 数据筛选匹配(Match):算法输入筛选规则陷门Tr和用于筛选的标签I。若匹配成功,算法输出“1”;否则,输出“0”。
2.4 安全需求
针对支持隐私保护的物联网数据筛选方案,其安全需求主要包括支持物联网数据发送设备身份隐私保护、保证密文完整有效和支持数据内容隐私保护。
支持物联网数据发送设备身份隐私保护就需要抵御针对设备身份的攻击,而这种攻击可以分为选择身份攻击和身份猜测攻击。选择身份攻击是针对筛选陷门中的身份信息进行攻击,攻击者挑战两个不同身份的数据发送端,在不能获得对应密钥和陷门的情况下判断筛选标签具体是这两个数据发送设备中的哪一个生成的;身份猜测攻击是针对筛选标签中的身份信息进行攻击,攻击者挑战两个不同身份的数据发送端,在不能获得对应密钥和标签的情况下判断筛选陷门具体是匹配这两个数据发送设备中的哪一个。
保证密文完整有效就需要保证密文签名的不可伪造,必须将筛选标签和加密物联网数据进行绑定来生成签名,通过签名验证来确认加密物联网数据的真实有效,其安全模型类似于抵抗一次性签名伪造攻击。
支持数据内容隐私保护就需要保证数据的机密性,必须对数据进行加密,以防止数据内容明文发送而导致数据内容泄露。
3 系统方案
3.1 方案构建
文中提出的方案包含以下8个部分:
(1) 系统设置(Setup):可信第三方生成系统参数(G,p,g),其中p为质数,g是循环群G的一个生成元。选择一个安全对称加密算法E(K,data),其中K是对称加密密钥,data是明文。抗碰撞的哈希函数H0、H1、H2,其中H0:{0,1}*→ Z*p,H1:{0,1}*→ Z*p,H2:{0,1}*×G×G→ Z*p。
(2) 密钥生成:
① KeygenT:可信第三方随机选取一个 Z*p上的随机数α,计算gα,则有系统主密钥(msk,mpk)=(α,gα)。
② KeygenA:可信第三方随机选取两个 Z*p上的随机数rA和tA,其中令skA=rA,计算p kA0= grA,p kA1= gtA,再根据A的身份IDA计算p kA2=rA+tA+H0(IDA‖skA‖p kA1),销毁tA。可信第三方通过安全信道将私钥skA分配给用户A。
③ KeygenB:可信第三方随机选取两个 Z*p上的随机数rB和tB,其中令skB=rB,计算p kB0= grB,p kB1= gtB,再根据B的身份IDB计算p kB2=rB+tB+H0(IDB‖skB‖p kB1),销毁tB。可信第三方通过安全信道将私钥skB分配给设备B。
(3) 密钥验证(Check):用户A和设备B在收到自己的私钥后,均可完成私钥认证,方法相同。以设备B为例,判断 gpkB2=p kB0p kB1mp kH0(IDB‖skB‖pkB1)是否成立。若成立,skB是有效密钥,算法输出“1”;否则skB不是有效密钥,输出“0”。
(4) 筛选陷门生成(Trapdoor):用户A生成数据对称解密密钥K=pk rAB0= grArB。用户A再随机选取一个 Z*p上的随机数x,结合时戳t,计算Tr1=xH1(K‖t)+rA,Tr2=p kxB0,Tr3=gx。用户A将筛选陷门 Tr=(Tr1,Tr2,Tr3)发送给中继节点设备组。
(5) 数据密文和筛选标签生成(Index):设备B生成数据对称加密密钥K=pk rBA0= grArB,再使用安全的对称加密算法E对原始物联网数据data加密得到加密物联网数据m=E(K,data)。设备B再随机选取一个 Z*p上的随机数y,结合时戳t,计算I1=yH1(K‖t)+rB,I2=p kyA0,I3=gy。
(6) 完整性签名生成(Sign):设备B随机选取一个 Z*p上的随机数θ,计算σ1=θ+yH2(m,I3,gθ),σ2=H2(m,I3,gθ)。设备B将标签I=(I1,I2,I3)、用对称加密密钥K对数据加密得到的物联网数据m、用于保证数据完整性的签名σ=(σ1,σ2)一起打包发送给物联网中继节点设备。
(7) 完整性签名验证(Verify):物联网中继节点设备判断等式H2(m,I3, gσ1/ Iσ23)=σ2是否成立。若成立,σ是有效签名,算法输出“1”;否则,σ不是有效签名,输出“0”。
(8) 数据筛选匹配(Match):物联网中继节点设备判断等式 ITr13Tr2=T rI13I2是否成立。若成立,匹配成功,则算法输出“1”;否则,输出“0”。当输出结果为“1”时,中继节点设备将对应的数据按策略转发到存储服务器对应的存储位置。用户A可以通过访问对应的数据存储位置得到加密物联网数据m,再用对称密钥K解密得到相应的物联网数据data。
3.2 正确性推导
密钥验证正确性推导过程如下所示:
| pkB0pkB1mpkH0(IDB‖skB‖pkB1)=grBgtBgαH0(IDB‖skB‖pkB1)=grB+tB+αH0(IDB‖skB‖pkB1)=gpkB2 。 | (1) |
完整性签名验证正确性推导过程如下所示:
| H2(m,I3,gσ1/Iσ23)=H2(m,gy,gθ+yH2(m,I3,gθ)/gyH2(m,I3,gθ))=H2(m,I3,gθ)=σ2 。 | (2) |
数据筛选匹配正确性推导过程如下所示:
| ITr13Tr2=gy(xH1(K‖t)+rA)pkxB0=gy(xH1(K‖t)+rA)grBx=gxyH1(K‖t)+rAy+rBx=Unknown node type: break gx(yH1(K‖t)+rB)grAy=gx(yH1(K‖t)+rB)pkyA0=TrI13I2 。 | (3) |
4 方案评估分析
4.1 执行效率评估分析
为了更接近真实的物联网,实验环境使用了PC端和可用于模拟工控终端的Raspberry Pi。具体实验环境如下:PC端使用了Intel Core i7-7700处理器,其CPU为4核3.60 GHz主频,内存为4 GB,操作系统为Ubuntu 14.04.3;Raspberry Pi使用ARMv7处理器,同时CPU的主频和内存分别被限制为600 MHz和128 MB,操作系统为Ubuntu MATE 16.04。为了更接近物联网应用实际情况,其中PC端用于模拟系统可信第三方和用户,而Raspberry Pi用于模拟物联网中继节点设备和数据发送设备。实验使用了PBC库来实现相关椭圆曲线计算,并且选用了A型椭圆曲线:y2=x3+x,其中有|Zp|=160比特,|G1|=512比特,|G2|=1 024比特。效率执行分析主要分为计算开销和通信开销。
4.1.1 计算开销
为更实际的评估开销,将以系统架构中的参与者为主体进行计算开销分析。所计算开销主要从私钥生成、密钥验证、筛选陷门生成、筛选标签和完整性签名生成、完整性签名验证和数据筛选匹配5个方面进行分析。其中,密钥会分别分配给用户和数据发送端,从用户主体(PC模拟)和数据发送端主体(Raspberry Pi模拟)两个方面来分别进行密钥验证的计算开销分析。此外,筛选标签生成中的物联网数据加密可以与文献[
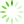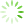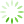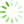
图2 实验效率图
4.1.2 通信开销
通信和存储开销分析如
| 方案 | 文献[ | 文中方案 |
|---|---|---|
| 私钥 | |G1| | |Zp| |
| 陷门 | 2|G1| | |Zp|+2|G1| |
| 标签 | 2|Zp|+2|G1| | 3|Zp|+2|G1| |
在私钥方面,考虑到在实际物联网数据发送设备中需要可信存储空间来存储设备私钥,所提方案所布置的物联网数据发送设备对可信存储空间的需求较小,其设备制造成本更低,更具有存储优势,同时也更符合物联网应用。
在标签方面,尽管所提方案的通信开销有所增加,|Zp|=160比特,但在实际的物联网布置中,通常以每个中继节点设备只管理一个小范围区域的数据发送设备的方式进行设备管理,而每个数据发送设备和中继节点设备之间的数据传输多采用无线或有线网络连接,由于这种传输方式速度较快,故其增加的数据传输消耗很低,可以忽略,并不影响物联网的实际运行。因此,这些增加的通信开销是可以容忍的。
在陷门方面,尽管所提方案的存储开销会增加|Zp|=160比特,但在实际的物联网布置中,通常以每个中继节点设备只管理一个小范围区域的数据发送设备的方式进行设备管理,每个中继节点设备所存的筛选陷门数量较少,且这些陷门不需要秘密存储,故其增加的存储消耗也较少,可以忽略。因此,这些存储开销是可以容忍的。
此外,对比文献[
综上所述,所提方案相比于已有的方案[
4.2 安全性分析
根据安全需求可以发现,所提方案需对物联网设备的身份信息实现隐私保护,即需能抵抗选择身份攻击和身份猜测攻击;本方案需保证密文完整有效,即需能抵抗密文签名伪造攻击;本方案还需提供对数据内容隐私保护,即需要通过数据的加密来保证数据内容的机密性。
在抵抗选择身份攻击方面,攻击者选定用户的身份为A,两个数据发送设备的身份为B1、B2。构建安全游戏如下:限定敌手不能询问A、B1、B2的私钥,同时可以发起除了从B1到A和B2到A的任何筛选陷门生成和筛选标签生成询问,最后挑战者从身份B1和B2中选择一个Bw,计算并返回相应的标签。敌手需要根据所收到的标签I1=yH1( KBωA‖t)+ rBω,I2=p kyA0,I3=gy,判断出ω∈{0,1} 的值。首先,由于敌手不能询问A、B1、B2私钥和从B1到A与B2到A的任何筛选陷门生成及筛选标签,敌手不能从前置的询问中获得更多的有效信息。然后可以分两种情况讨论:① 由求解目标中 KBωA= grBωrA与A、B1、B2的公钥 grA、 grB1、 grB2可以得知,敌手需要解决判定性Diffie-Hellman困难问题才能猜测成功;② 由求解目标中$\mathrm{pk}_{B_{\omega_{0}}}^{x}$与B1、B2的公钥 grB1, grB2和g可以得知,敌手需要解决离散对数求解困难问题才能猜测成功。
在抵抗身份猜测攻击方面,攻击者选定用户的身份为A,两个数据发送设备的身份B1、B2。构建安全游戏如下:限定敌手不能询问A、B1、B2的私钥,同时可以发起除了从B1到A和B2到A的任何筛选陷门生成及筛选标签生成询问,最后挑战者从身份B1和B2中选择一个Bw,并计算相应的陷门。敌手需要根据所收到的陷门Tr1=xH1( KBωA‖t)+rA,Tr2=pkx Bω0,Tr3=gx,判断出ω∈{0,1} 的值。首先,由于敌手不能询问A、B1、B2的私钥和从B1到A与B2到A的任何筛选陷门生成及筛选标签,敌手不能从前置的询问中获得更多的有效信息。然后可以分两种情况讨论:① 由求解目标中 KBωA= grBωrA与A、B1、B2的公钥 grA、 grB1、 grB2可以得知,敌手需要解决判定性Diffie-Hellman困难问题才能猜测成功;② 由求解目标中pkx Bω0与B1、B2的公钥 grB1、 grB2和gx可以得知,敌手需要解决判定性Diffie-Hellman困难问题才能猜测成功。
抵抗密文签名伪造攻击方面,攻击者针对签名进行伪造,构建安全游戏如下:限定敌手只能对新的数据密文m和新的筛选标签I进行签名伪造。敌手需要伪造出签名σ1=θ+yH2(m,I3,gθ),σ2=H2(m,I3,gθ),该签名可使得验证等式H2(m,I3, gσ1/ Iσ23)=σ2成立。首先,尽管敌手可以询问密钥、筛选陷门、筛选标签,但该签名方案类似于一次性签名方案,由数据密文m与新的筛选标签I的新鲜性可以得知,敌手并不能从前置的询问中获得更多的有效信息。然后由求解目标中生成σ1需要y,与由筛选标签I的新鲜性仅能得到I3=gy和g可以得知,敌手需要解决离散对数求解困难问题才能攻击成功。
保证数据的机密性方面,采用了对称加密的方法,若敌手能攻破所提方案等同于敌手具备攻破所选安全对称加密算法的能力。
综上所述,由于攻击者需具备解决离散对数困难问题、判定性Diffie-Hellman问题、选定安全对称加密算法中至少一项的能力,才能攻破所提出的方案,因此文中所提方案能够满足设备身份隐私保护、密文完整有效和数据内容隐私保护等性质。
5 结束语
笔者提出了一个保护设备身份隐私的物联网数据筛选方案。该方案通过在物联网中继设备节点放置筛选陷门来设定数据筛选规则,在支持设备身份隐私保护、密文完整有效和数据内容隐私保护的基础上,实现了对物联网数据按设备身份进行数据筛选和分流的功能。实验结果显示,该方案的执行效率更高,适合于物联网数据安全管理的应用。
参考文献
吴振豪, 高健博, 李青山, 等. 数据安全治理中的安全技术研究[J]. 信息安全研究, 2021, 7(10):907-914. [百度学术]
WU Zhenhao, GAO Jianbo, LI Qingshan, et al. Research on Security Technology in Data Security Governance[J]. Journal of Information Security Research, 2021, 7(10):907-914. [百度学术]
LYU L J, NANDASKUMAR K, RUBINSTEIN B, et al. PPFA:Privacy Preserving Fog-Enabled Aggregation in Smart Grid[J]. IEEE Transactions on Industrial Informatics, 2018, 14(8):3733-3744. DOI:10.1109/TII.9424https://ieeexplore.ieee.org/xpl/RecentIssue.jsp?punumber=9424 [百度学术]
GE C P, YIN C C, LIU Z, et al. A Privacy Preserve Big Data Analysis System for Wearable Wireless Sensor Network[J]. Computers & Security, 2020(96):1-10. [百度学术]
侯戌非. 物联网环境下海量多源异构数据的存储算法[J]. 宁夏师范学院学报, 2022, 43(7):80-85. [百度学术]
HOU Xufe. The Storage Algorithm of Multi-Source Heterogeneous Data in Internet of Things Environment[J]. Journal of Ningxia Normal University, 2022, 43(7):80-85. [百度学术]
杨颜博, 张嘉伟, 马建峰. 一种使用区块链保护车联网数据隐私的方法[J]. 西安电子科技大学学报, 2021, 48(3):21-30. [百度学术]
YANG Yanbo, ZHANG Jiawei, MA Jianfeng. Method for Using the Blockchain to Protect Data Privacy of IoV[J]. Journal of Xidian University, 2021, 48(3):21-30. [百度学术]
SHEN H, ZHANG M W, WANG H, et al. A Lightweight Privacy-Preserving Fair Meeting Location Determination Scheme[J]. IEEE Internet of Things Journal, 2020, 7(4):3083-3093. DOI:10.1109/JIoT.6488907https://ieeexplore.ieee.org/xpl/RecentIssue.jsp?punumber=6488907 [百度学术]
SHERRY J, LAN C, POPA R A, et al. BlindBox:Deep Packet Inspection over Encrypted Traffic[J]. ACM Sigcomm Computer Communication Review, 2015, 45(4):213-226. DOI:10.1145/2829988.2787502https://dl.acm.org/doi/10.1145/2829988.2787502 [百度学术]
NING J T, POH G S, LOH J C, et al. PrivDPI:Privacy-Preserving Encrypted Traffic Inspection with Reusable Obfuscated Rules[C]// ACM Conference on Computer and Communications Security. New York: ACM, 2019:1657-1670. [百度学术]
TANG Q, PEJO B, WANG H. Protect both Integrity and Confidentiality in Outsourcing Collaborative Filtering Computations[C]// IEEE International Conference on Cloud Computing.Piscataway:IEEE, 2016:941-946. [百度学术]
MCCANNE S, JACOBSON V. The BSD Packet Filter:A New Architecture for User-Level Packet Capture[C]// USENIX Winter Conference on USENIX Winter Conference.Berkeley:USENIX, 1993:259-270. [百度学术]
LEE C H, CHUANG C W. Efficient Search in Graph Databases Using Cross Filtering[J]. Information Sciences, 2014, 286:1-18. DOI:10.1016/j.ins.2014.06.047https://linkinghub.elsevier.com/retrieve/pii/S002002551400704X [百度学术]
LIU J X, TANG M D, ZHENG Z B, et al. Location-Aware and Personalized Collaborative Filtering for Web Service Recommendation[J]. IEEE Transactions on Services Computing, 2016, 9(5):686-699. DOI:10.1109/TSC.4629386https://ieeexplore.ieee.org/xpl/RecentIssue.jsp?punumber=4629386 [百度学术]
OGONJI M M, OKEYO G, WAFULA J M. A Survey on Privacy and Security of Internet of Things[J]. Computer Science Review, 2020, 38(7):100312. DOI:10.1016/j.cosrev.2020.100312https://linkinghub.elsevier.com/retrieve/pii/S1574013720304123 [百度学术]
曾勇, 吴正远, 董丽华, 等. 加密流量中的恶意流量识别技术[J]. 西安电子科技大学学报, 2021, 48(3):170-187. [百度学术]
ZENG Yong, WU Zhengyuan, DONG Lihua, et al. Research on Malicious Traffic Identification Technology in Encrypted Traffic[J]. Journal of Xidian University, 2021, 48(3):170-187. [百度学术]
JIANG P, WANG Q, HUANG M, et al. Building In-the-Cloud Network Functions:Security and Privacy Challenges[J]. Proceedings of the IEEE, 2021, 109(12):1888-1919. DOI:10.1109/JPROC.2021.3127277https://ieeexplore.ieee.org/document/9645060/ [百度学术]
OSTROVSKY R, SKEITH. III W E. Private Searching on Streaming Data[J]. Journal of Cryptology, 2007, 20(4):397-430. DOI:10.1007/s00145-007-0565-3http://link.springer.com/10.1007/s00145-007-0565-3 [百度学术]
YUAN X L, WANG X Y, LIN J X, et al. Privacy-Preserving Deep Packet Inspection in Outsourced Middleboxes[C]// In 35th Annual IEEE International Conference on Computer Communications,INFOCOM 2016.Piscataway:IEEE, 2016:1-9. [百度学术]
KIM J, CAMTEPE S, BAEK J, et al. P2DPI:Practical and Privacy-Preserving Deep Packet Inspection[C]// ASIA CCS 21:ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021:135-146. [百度学术]
NING J, HUANG X, POH G S, et al. Pine:Enabling Privacy-Preserving Deep Packet Inspection on TLS with Rule-Hiding and Fast Connection Establishment[C]// European Symposium on Research in Computer Security.Berlin:Springer, 2020:3-22. [百度学术]
WEN J, LIU J, WU A, et al. A General Framework for Matching Pattern Hiding in Deep Packet Inspection[C]// International Conference on Information Security Applications.Berlin:Springer, 2021:243-254. [百度学术]
REN H, LI H W, LIU D X, et al. Privacy-Preserving Efficient Verifiable Deep Packet Inspection for Cloud-Assisted Middlebox[J]. IEEE Transactions on Cloud Computing, 2022, 10(2):1052-1064. DOI:10.1109/TCC.2020.2991167https://ieeexplore.ieee.org/document/9082166/ [百度学术]
REN H, LI H W, LIU D X, et al. Enabling Secure and Versatile Packet Inspection with Probable Cause Privacy for Outsourced Middlebox[J]. IEEE Transactions on Cloud Computing, 2022, 10 (4):2580-2594. DOI:10.1109/TCC.2021.3059026https://ieeexplore.ieee.org/document/9354035/ [百度学术]
BONEHD, CRESCENZO G D, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// International Conference on the Theory and Applications of Cryptographic Techniques.Berlin:Springer, 2004:506-522. [百度学术]
JING P, GUO F C, SUSILO W, et al. Keyword Attacks and Privacy Preserving in Public-Key-Based Searchable Encryption[J]. Encyclopedia of Big Data Technologies, 2019:1067-1087. [百度学术]
LU R, LIN X, LUAN T H, et al. PRefilter:An Efficient Privacy-Preserving Relay Filtering Scheme for Delay Tolerant Networks[C]// International Conference on Computer Communications.Piscataway:IEEE, 2012:1395-1403. [百度学术]
WANG X F, MU Y, CHEN R M. Privacy-Preserving Data Packet Filtering Protocol with Source IP Authentication[J]. Wireless Personal Communication, 2017, 95:3509-3537. DOI:10.1007/s11277-017-4010-0http://link.springer.com/10.1007/s11277-017-4010-0 [百度学术]
JING P, GUO F C, SUSILO W, et al. PPFilter:Provider Privacy-Aware Encrypted Filtering System[J]. IEEE Transactions on Services Computing, 2021, 14(5):1519-1530. DOI:10.1109/TSC.2018.2873656https://ieeexplore.ieee.org/document/8481589/ [百度学术]
102
浏览量
88
下载量
0
CSCD
相关文章
相关作者
相关机构
